Defending systems against cyberattacks is no longer just about securing an individual firm — it is about strengthening the entire supply chain
Dallas and Tokyo—Cyberattacks and new threats are changing the automotive landscape as vehicle complexity increases and connectivity, automation and advanced driver assistance systems (ADAS) create vulnerabilities. A new report by VicOne, an automotive cybersecurity solutions provider, offers perspective on today’s cybersecurity challenges for OEMs and suppliers, and how they might develop strategies to navigate those complexities.
“In our analysis of the threat landscape, we noticed that the losses from cyberattacks in the first half of the year exceeded $11 billion, marking an unprecedented surge compared to the last two years,” states the report. “A closer examination reveals that these cyberattacks predominantly targeted automotive suppliers, indicating a rising trend.
“Alarmingly, over 90% of these attacks were not aimed at OEMs themselves but rather at other entities in the supply chain. Attackers often find it difficult to penetrate well-protected companies, so they target less vigilant firms instead. But OEMs are affected all the same, because of the supply chain disruptions. Consequently, defending systems against cyberattacks is no longer just about securing an individual firm; it is about strengthening the entire supply chain.”
KEY TAKEAWAYS AND HIGHLIGHTS
Regulation continues to be a pivotal force in automotive industry trends
• The main challenge lies in implementing cybersecurity solutions effectively in automotive environments.
• It is vital to address how cybersecurity and automotive experts can effectively implement security assessment in the automotive industry.
Cyberattacks on the automotive industry are on the rise
• Exploiting vulnerabilities in the supply chain has become a prevalent trend in cyberattacks, with a focus on targeting third-party suppliers.
• A rising number of reported vulnerabilities suggest a growing interest in the automotive industry
Vehicle data constitutes an overlooked yet growing facet of the automotive industry
• Security gaps observed in automotive data indicate how it can be compromised.
• There is a regulatory vacuum when it comes to vehicle data that needs to be resolved.
A Rise in Cyberattacks and Security Incidents
In addition to vulnerabilities inherent in vehicles or their systems, the analysis gathered a significant number of automotive incident cases and categorized them. The majority of the cases involved cyberattacks, immobilizer problems, and concerns related to applications and application programming interfaces (APIs).
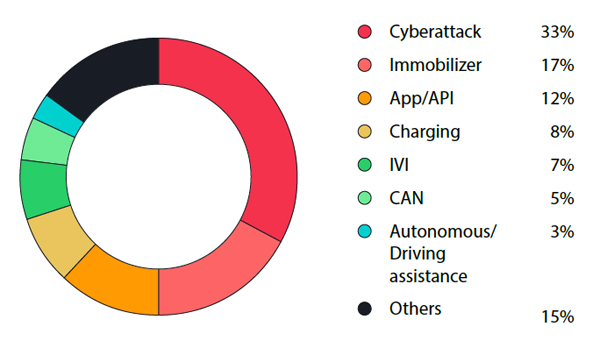
The distribution of security incident case categories from the second half of 2022 to the first half
of 2023.
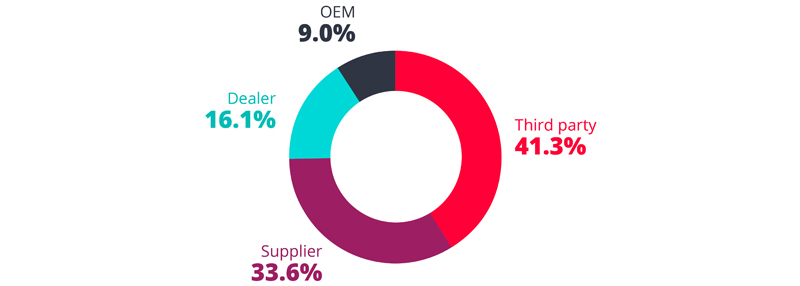
“Upon closer examination of the cyberattack incidents,” states the report, “it becomes clear that a significant number of these cases have their origins in third-party providers of services and diagnostics, and suppliers of automotive components.” Among those are manufacturing companies, logistics providers, service providers, and companies engaged in the production of components, accessories, or parts.
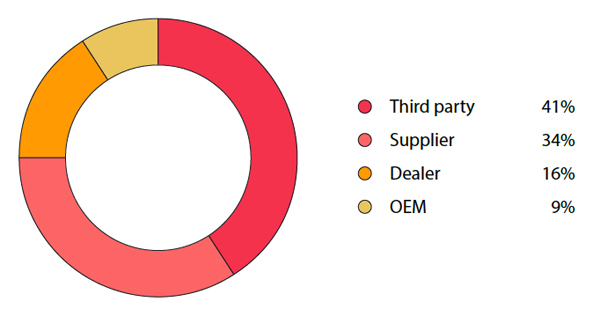
The distribution of cyberattack case categories from the second half of 2022 to the first half of 2023.
CAN Bus Injection
CAN bus injection is among the top threats reported in the first half of 2023, according to the study. It makes it easier for potential attackers to steal a vehicle and has been used often by criminals this year. It influences two kinds of threats: the CAN bus and immobilizers, which considerably impact vehicle design. The study outlines the following attack scenario that’s possible using this method:
• A potential attacker accesses the CAN bus wiring, through the headlights, to which the smart key receiver electronic control unit (ECU) is connected.
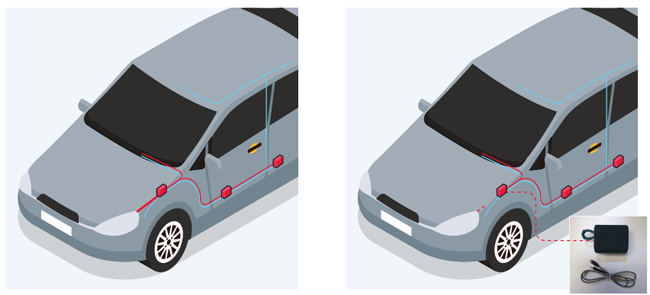
Left: The headlight is still connected to the vehicle’s CAN bus. Right: It is replaced by the CAN injector.
• Once the CAN injector is powered on, a potential attacker can send a wake-up frame to wake the CAN bus repeatedly until the device receives a response.
• After receiving the response, the CAN injector engages the dominant-override circuit caused by the arbitration mechanism. This circuit blocks other devices from transmitting on the CAN bus and disables the error mechanism of the CAN bus protocol, preventing other ECUs from stopping the CAN injector and bypassing some security hardware.
• The CAN injector, now pretending to be the smart key ECU, sends a fake message, such as “Key is validated, unlock immobilizer,” in bursts to the vehicle’s gateway ECU.
• The gateway ECU copies the fake message over to another CAN bus.
“It’s clear that the automotive industry needs to give higher priority to cybersecurity, in terms of resources and budget,” said Max Cheng, chief executive officer of VicOne. “That is something that must be happening continually — building up the processes, building up the organization, building up the talent, building up the entire system — or you will never be able to implement cybersecurity effectively.”
VicOne Automotive Cyberthreat Landscape Report 2023 is available at https://vicone.com/reports/automotive-cybersecurity-report-2023.










Comments are closed.